
The more data you have about your consumers, the better you can understand their needs. However, while you store or manage their data, your consumers expect that you protect it adequately.
A data risk assessment tells you if you’re doing a solid job of protecting their data from all the potential threats present in and outside your organization.
Let’s learn more about what it is, why it’s important, and how to conduct it in this article.
Key Takeaways
Data risk assessment (DRA) is a process of reviewing and improving the security of data under your control
It can help you improve your security measures and minimize the risk of internal and external threats
When performing a data risk assessment, be sure to take a data inventory, classify sensitive data, prioritize them, review your data security protocols, and identify current vulnerabilities as well as document the process and communicate with shareholders
What is Data Risk Assessment?

Data risk assessment is a process of reviewing data under the control of your business and recommending improvements to safeguard it.
That includes all sensitive data you store, manage, or have access to across your entire IT ecosystem (websites, servers, cloud, etc.)
On the other hand, to evaluate the risks involved in transferring data to 3rd-party providers or with potential privacy risks in processing data, you would conduct either a data transfer impact assessment (DTIA) or a data privacy impact assessment (DPIA) also commonly referred to as a Data Protection Impact Assessment (DPIA).
Why is Data Risk Assessment Important?
DRA helps in several ways, from identifying potential risks to enhancing customer trust. Here are all the ways they are important:
Helps to identify potential data risks: Knowing this can better prepare your business to take proactive measures to prevent data breaches, unauthorized access, data loss, and more.
Better resource allocation. Knowing which sensitive data has priority lets you better focus your efforts and resources where they are most needed.
Protecting sensitive data. DRA helps you identify sensitive data that your business manages, including personal, financial, or other information, including how it is stored, who has access to it, and more
It re-evaluates your current security measures. A good DRA will also tell you if your current security measures are lacking and what areas you could improve.
DRA ensures regulatory compliance. A data risk assessment will also pinpoint areas of non-compliance and suggest what measures you can take to address them and avoid fines.
Finally, it enhances consumer trust. By performing data risk assessment regularly and taking the necessary steps to improve your data security, you will maintain consumer trust and build positive long-term relationships with them.
How to Perform a Data Risk Assessment
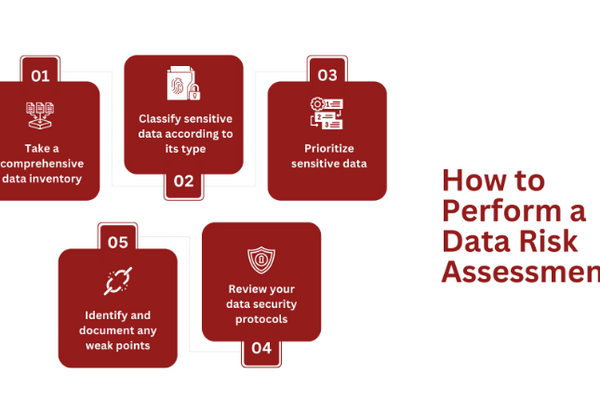
How your business performs a DRA will depend on its specific needs.
But these are the general five steps to perform a DRA:
1. Take a comprehensive data inventory
A data inventory is an up-to-date and detailed log of all your data assets, data sources, and other information about that data.
This helps you make more informed decisions, mitigate risks and ensure corporate compliance with data privacy laws like CCPA or GDPR.
2. Classify sensitive data according to its type
“Sensitive data” is an umbrella term, but each type requires different privacy and security measures.
GDPR considers the following personal data as “sensitive”:
Personal data revealing racial/ethnic origin and/or political/religious/philosophical beliefs and opinions
Health-related data
Genetic data such as biometric data (fingerprint, iris scan) that can identify a person
Sex and sexual orientation data
Trade-union membership
For instance, you might need different processes and protocols for personal health data than biometric data.
3. Prioritize sensitive data
The more sensitive data you have to process, the harder it will be to know which data requires more attention. As a result, you have to use more resources than necessary.
Prioritizing sensitive data will remove much of the guesswork in the data risk assessment process and can significantly speed it up.
4. Review your data security protocols
Next, you need to take a good look at your current data security protocols and see where you can improve them
For example, you can limit or better define the use of password generators (an increase from 8 characters minimum to 12) or raise more awareness of phishing in your employees.
5. Identify and document any weak points you find
Data risk assessment is about finding data risks, not correcting them. However, it’s still vital for this as it can pinpoint exact security weak points that you should pay attention to.
Of course, once you conduct a data risk assessment, your work is far from finished. Now you need to take what you just learned from it and take action to better secure your customer data.
Best Practices for Data Risk Assessment
Here are the best practices that will help you better ascertain your potential data risks when performing a DRA:
Focus your resources and efforts by clearly defining the scope of your data risk assessment
Take a detailed inventory of all your data assets
Prioritize data by potential risk
Include potential internal (unauthorized access, poor passwords, etc.) and external (malware, hackers, etc.) threats
Review your data security protocols, including physical security, authentication, encryption, etc., to identify weak points
Improve your security protocols based on the previous step
Communicate with the stakeholders and the different departments in your organization so that everyone is on the same page
Constantly monitor and regularly perform a DRA
Closing
Knowing what data are potentially vulnerable can remove the guesswork when protecting it. As a result, knowing that their data is safe with your business, your consumers will trust you more with it.
Captain Compliance can help you better understand which sensitive data require your attention more and to become compliant in your area.
Get in touch with us today and make sure your company is fully compliant with the data privacy laws in your area.
Key Steps in a Data Risk Assessment:
-
Define Scope and Objectives: Clearly define the scope of the assessment (e.g., specific data types, systems, or departments) and the objectives (e.g., compliance, security improvement).
-
Data Identification and Classification: Identify all data assets and classify them based on sensitivity (e.g., confidential, public). Consider the type of data (PII, financial, health, etc.) and where it’s stored.
-
Threat Identification: Identify potential threats that could exploit vulnerabilities and compromise data. Examples include:
- Malicious Actors: Hackers, cybercriminals, insiders.
- Accidental Loss: Human error, hardware failure, software bugs.
- Natural Disasters: Fires, floods, earthquakes.
- Physical Theft: Stolen devices, documents.
- Social Engineering: Phishing, pretexting.
-
Vulnerability Assessment: Evaluate existing security controls and identify weaknesses in systems, processes, and people. Consider:
- Technical Vulnerabilities: Software flaws, unpatched systems, weak passwords.
- Administrative Vulnerabilities: Lack of policies, inadequate training, insufficient access controls.
- Physical Vulnerabilities: Unsecured facilities, lack of surveillance.
-
Risk Analysis: Analyze the likelihood and impact of each identified risk. A common approach is to use a matrix that plots likelihood against impact (low, medium, high) to determine the overall risk level.
-
Risk Evaluation and Prioritization: Evaluate the overall risk level for each data asset and prioritize risks based on their potential impact on the organization.
-
Risk Response: Develop and implement risk mitigation strategies. Options include:
- Risk Avoidance: Stop the activity that creates the risk.
- Risk Mitigation: Implement controls to reduce the likelihood or impact of the risk.
- Risk Transfer: Transfer the risk to a third party (e.g., insurance).
- Risk Acceptance: Accept the risk if the cost of mitigation outweighs the potential impact.
-
Documentation and Reporting: Document the entire risk assessment process, including identified risks, vulnerabilities, and mitigation strategies. Communicate findings to relevant stakeholders.
-
Monitoring and Review: Regularly monitor the effectiveness of implemented controls and review the risk assessment to ensure it remains current and relevant. The threat landscape and business environment are constantly changing, so regular reviews are crucial.
Tools and Techniques:
- Questionnaires and Surveys: Gather information from employees and stakeholders.
- Vulnerability Scanners: Identify technical weaknesses in systems.
- Penetration Testing: Simulate attacks to test security controls.
- Data Flow Diagrams: Visualize how data moves through the organization.
- Risk Management Frameworks: Use established frameworks like NIST Cybersecurity Framework or ISO 27005.
Key Considerations:
- Data Privacy Regulations: Consider relevant data privacy regulations (e.g., GDPR, CCPA) when conducting the assessment.
- Business Impact Analysis: Integrate the data risk assessment with a business impact analysis to understand the potential impact of data loss on business operations.
- Collaboration: Involve stakeholders from different departments (IT, legal, compliance, business units) in the process.
A well-conducted data risk assessment is essential for protecting sensitive data and maintaining business continuity. It’s an ongoing process that should be regularly reviewed and updated to keep pace with evolving threats and regulatory requirements.
FAQs
What is a Data Risk Assessment?
Data risk assessment is a process that involves reviewing data under the control of your business and recommending improvements to safeguard it.
How Do You Conduct a Data Risk Assessment?
There are several ways to conduct a data risk assessment. Here are five steps you can do:
Take a data inventory
Classify sensitive data
Prioritize sensitive data
Review your data security protocols
Identify and document weak points
What is an Example of Data Risk?
Data risks can be internal and external.
An example of an internal data risk would be an employee using a weak password or sharing their credentials.
On the other hand, an external data risk would be a phishing attack, malware, or a DDoS attack aimed to cause a data breach.
What is a GDPR Risk Assessment?
A GDPR risk assessment is a process of identifying and evaluating potential data security risks under the GDPR.
Does GDPR Require a Risk Assessment?
Yes. Specifically, Article 35: Data protection impact assessment says that where data processing has a high risk to the “rights and freedoms of a natural person” an organization has to perform a risk assessment.
Do you want to be GDPR-compliant and start off with a data risk assessment. Book a demo today or do a free data privacy audit scan and see where gaps may be in your privacy program.